声明
本文仅作学习与交流, 如有侵权请联系删除.
文中使用的是从吾爱上下载的2.2.3.223, 刷视频/点赞/聊天/赚钱/评论/个人资料/搜索等功能均可正常使用.
(这玩意真的, 又老又新...... 本来还想逆一下sig3, 但是补环境实在让人发蒙...... 目前笔者感觉可行的方式就只有用frida调了)
(想找纯算__NS_sig3的可以直接关闭了, 本文只讨论使用Frida进行远程调用的可行性)
抓包
抓包环境
下载Reqable, 使用软件内自带的功能给手机安装系统根证书
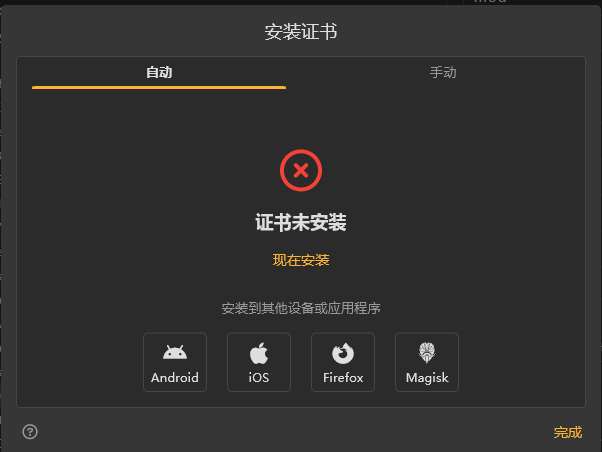
然后在手机中找到 设置 > WLAN > 然后点击你连的网络 > 代理
QUIC降级
此时你如果直接去抓的话你会发现, 抓不了一点, 只有okhttp的走了代理, 我们需要的一点没有, 所以我们需要Hook然后强制降级
Frida配置
下载hluda-server, 你从github上下载的frida会直接被检测 (快手直接闪退, 但是奇怪的一点是如果你用frida启动的话, 它不闪退但是提示无连接)
在电脑上安装Python环境, 安装frida (15.2.2)
pip install frida==15.2.2将hluda-server 放到手机的/data/local/tmp文件夹中, 并给执行权限, 然后执行 (需要root)
chmod 777 hluda-server
./hluda-server -l 0.0.0.0:1145 # 这里监听1145逆向
Jadx反编译, 并在代码中搜索cronetConfig 结果如下 (注: 在新版本也同样可以用这个思路) (为什么是思路呢, 因为我没试)
// Decompiled by Jadx
......
Aegon.m16466a(context, m62579a.m62584a("cronetConfig", "{}"), context.getCacheDir().getAbsolutePath(), new Aegon.AbstractC4618a() { // from class: com.kuaishou.gifshow.network.c.1
@Override // com.kuaishou.aegon.Aegon.AbstractC4618a
/* renamed from: a */
public final void mo16480a(String str) {
C33039ap.m122241a(str);
}
});
......可以看到, 配置文件在此传入 (在IDA中打开libageon.so并搜索字符串"enable_quic"可以找到相关逻辑)
// IDA Decompiled
int __fastcall sub_C5604(const char *a1, const char *a2, int *a3)
{
if ( a1 && a2 )
{
// ......
if ( v97[0] == 6 )
{
// ......
if ( sub_15D3CC(v97, "preconnect_interval", 19, 2, 200) )
{
v16 = ((int (*)(void))sub_15D25C)();
if ( (unsigned int)(v16 + 1) < 0x36EE82 )
v107 = v16;
}
if ( sub_15D3CC(v97, "preconnect_num_streams", 22, 2, v62) )
{
v17 = ((int (*)(void))sub_15D25C)();
if ( v17 <= 0x10 )
v108 = v17;
}
if ( sub_15D3CC(v97, "preconnect_non_altsvc", 21, 1, v63) )
v109 = sub_15D22C();
if ( sub_15D3CC(v97, "preconnect_on_background", 24, 1, v64) )
v110 = sub_15D22C();
if ( sub_15D3CC(v97, "preconnect_urls", 15, 7, v65) )
{
v19 = *(_QWORD *)((int (*)(void))sub_15D318)();
for ( i = (_BYTE *)v19; (_BYTE *)HIDWORD(v19) != i; i += 16 )
{
// ......
}
}
if ( sub_15D3CC(v97, "preconnect_group_id_whitelist", 29, 7, v66) )
{
v22 = *(_QWORD *)((int (*)(void))sub_15D318)();
for ( j = (_BYTE *)v22; (_BYTE *)HIDWORD(v22) != j; j += 16 )
{
// ......
}
}
if ( sub_15D3CC(v97, "enable_quic", 11, 1, v67) )
v117 = sub_15D22C();
if ( sub_15D3CC(v97, "enable_brotli", 13, 1, v68) )
v118 = sub_15D22C();
if ( sub_15D3CC(v97, "enable_http2", 12, 1, v69) )
v119 = sub_15D22C();
if ( sub_15D3CC(v97, "quic_host_whitelist", 19, 7, v70) )
{
v25 = *(_QWORD *)((int (*)(void))sub_15D318)();
for ( k = (_BYTE *)v25; (_BYTE *)HIDWORD(v25) != k; k += 16 )
{
// ......
}
}
if ( sub_15D3CC(v97, "quic_hostport_forcelist", 23, 7, v71) )
{
v28 = *(_QWORD *)((int (*)(void))sub_15D318)();
for ( m = (_BYTE *)v28; (_BYTE *)HIDWORD(v28) != m; m += 16 )
{
// ......
}
}
if ( sub_15D3CC(v97, "quic_prefer_plaintext", 21, 1, v72) )
v126 = sub_15D22C();
if ( sub_15D3CC(v97, "quic_use_bbr", 12, 1, v73) )
v127 = sub_15D22C();
if ( sub_15D3CC(v97, "quic_idle_timeout_sec", 21, 2, v74) )
{
v30 = ((int (*)(void))sub_15D25C)();
if ( (unsigned int)(v30 - 5) <= 0xE0B )
v128 = v30;
}
if ( sub_15D3CC(v97, "ssl_session_cache_max", 21, 2, v75) )
{
v31 = ((int (*)(void))sub_15D25C)();
if ( v31 <= 0x80 )
v129 = v31;
}
if ( sub_15D3CC(v97, "proxy_host_blacklist", 20, 7, v76) )
{
v33 = *(_QWORD *)((int (*)(void))sub_15D318)();
for ( n = (_BYTE *)v33; (_BYTE *)HIDWORD(v33) != n; n += 16 )
{
// ......
}
}
if ( sub_15D3CC(v97, "socket_pool_max", 15, 2, v77) )
{
v35 = ((int (*)(void))sub_15D25C)();
if ( (unsigned int)(v35 - 1) <= 0x3E6 )
v133 = v35;
}
if ( sub_15D3CC(v97, "socket_pool_max_per_host", 24, 2, v78) )
{
v36 = ((int (*)(void))sub_15D25C)();
if ( (unsigned int)(v36 - 1) <= 0x62 )
v134 = v36;
}
if ( sub_15D3CC(v97, "disable_request_timeout", 23, 1, v79) )
v135 = sub_15D22C();
if ( sub_15D3CC(v97, "disable_throughtput_throttling", 30, 1, v80) )
v136 = sub_15D22C();
if ( sub_15D3CC(v97, "altsvc_broken_time_base", 23, 2, v81) )
{
v37 = ((int (*)(void))sub_15D25C)();
if ( (unsigned int)(v37 - 1) >> 4 <= 0xE0 )
v137 = v37;
}
if ( sub_15D3CC(v97, "altsvc_broken_time_max", 22, 2, v82) )
{
v38 = ((int (*)(void))sub_15D25C)();
if ( v38 - 1 <= (unsigned int)"_NOT_FOUND" )
v138 = v38;
}
if ( sub_15D3CC(v97, "cdn_preresolver_max_concurrent", 30, 2, v83) )
{
v39 = ((int (*)(void))sub_15D25C)();
if ( v39 <= 0x40 )
v139 = v39;
}
if ( sub_15D3CC(v97, "cdn_preresolver_priority_timeout_sec", 36, 2, v84) )
{
v40 = ((int (*)(void))sub_15D25C)();
if ( (unsigned int)(v40 - 5) <= 0xE0B )
v140 = v40;
}
if ( sub_15D3CC(v97, "http_cache_max_bytes", 20, 2, v85) )
{
v41 = ((int (*)(void))sub_15D25C)();
if ( v41 <= 0x40000000 )
v141 = v41;
}
if ( sub_15D3CC(v97, "connection_stats_interval", 25, 2, v86) )
{
v42 = ((int (*)(void))sub_15D25C)();
if ( (unsigned int)(v42 + 2) < 0x36EE83 )
v142 = v42;
}
if ( sub_15D3CC(v97, "quic_hints", 10, 7, v87) )
{
// ......
}
}
else
{
_android_log_print(6, "AegonNative", "Json config is not a dictionary");
}
sub_15EE70(v97);
sub_11AFE0(v98);
}
return _stack_chk_guard - v143;
}我们只要用Frida Hook即可
脚本
// 此脚本只适用于文中提供的快手apk
Java.perform(function () {
let C13458c = Java.use("com.kwai.sdk.switchconfig.c");
C13458c["a"].overload('java.lang.String', 'java.lang.String').implementation = function (str, str2) {
console.log(`C13458c.m62584a is called: str=${str}, str2=${str2}`);
if (str == "cronetConfig") {
str = "{\"enable_quic\": false, \"enable_http2\": false}" // 顺带把http2禁了
console.log("Replaced")
}
let result = this["a"](str, str2);
return result;
};
})效果
请求参数详解
(注: 不同版本, 不同接口的参数可能不同, 以你那抓到的为准)
有点废话, 不想看可以直接跳过
以下为GET参数:
POST参数:
sig, client_key, __NS_sig3, os, kuaishou.api_st, __NStokensig
(注: Sign生成时先生成sig, 然后__NStokensig, 最后是__NS_sig3)
sig参数
逆向
Jadx全局搜"sig", 可发现sig参数在com.yxcorp.retrofit.l.computeSignature中生成
参数来源
// 先调用C32925a.m121894b将GET参数和POST转为字符串, 然后传入CPU.getClock 请求侧代码不再展示
public final Pair<String, String> computeSignature(Request request, Map<String, String> map, Map<String, String> map2) {
return new Pair<>("sig", CPU.m108270a(C18220c.m79397a().mo83061b(), TextUtils.join("", C32925a.m121894b(map, map2)).getBytes(C35148a.f206923f), Build.VERSION.SDK_INT));
}
// map: GET参数, map2: POST参数 (也许吧, 不过不重要)
public static List<String> m121894b(Map<String, String> map, Map<String, String> map2) {
String value;
ArrayList arrayList = new ArrayList(map.size() + map2.size());
Iterator<Map.Entry<String, String>> it = map.entrySet().iterator();
// 升序排序后遍历map, 将参数转为key=value的形式放入arrayList
while (true) {
String str = "";
if (!it.hasNext()) {
break;
}
Map.Entry<String, String> next = it.next();
StringBuilder sb = new StringBuilder();
sb.append(next.getKey());
sb.append("=");
if (next.getValue() != null) {
str = next.getValue();
}
sb.append(str);
arrayList.add(sb.toString());
}
// 升序排序后遍历map2, 将参数转为key=value的形式放入arrayList
for (Map.Entry<String, String> entry : map2.entrySet()) {
StringBuilder sb2 = new StringBuilder();
sb2.append(entry.getKey());
sb2.append("=");
if (entry.getValue() == null) {
value = "";
} else {
value = entry.getValue();
}
sb2.append(value);
arrayList.add(sb2.toString());
}
// 使用字典序排序
try {
Collections.sort(arrayList);
} catch (Exception e) {
e.printStackTrace();
}
return arrayList;
}
算法
public abstract class CPU {
// 可以看到, 调用了libcore.so中的getClock函数, bArr即为上个函数获取的字节数组, i为ANDROID SDK版本
public static native String getClock(Context context, byte[] bArr, int i);
public static native String getMagic(Context context, int i);
static {
C33039ap.m122241a("core");
}
/* renamed from: a */
public static synchronized String m108270a(Context context, byte[] bArr, int i) {
String clock;
synchronized (CPU.class) {
clock = getClock(context, bArr, i);
}
return clock;
}
}进入libcore.so (话说IDA你认真的? 就这么水灵灵的把jint传进GetByteArrayElements了???? 真的百思不得其解)
(虽然但是, 这就一个有点咸的MD5 (加SALT了))
jstring __fastcall Java_com_yxcorp_gifshow_util_CPU_getClock(JNIEnv *a1, jobject _, jbyteArray a3, jint a4)
{
void *v7; // r8
JNIEnv v9; // r6
jbyte *v10; // r11
int v11; // r10
const char *v12; // r4
signed int v13; // r4
signed int i; // r11
jbyte *v15; // [sp+8h] [bp-C0h]
jint v16; // [sp+10h] [bp-B8h]
char v17[104]; // [sp+18h] [bp-B0h] BYREF
char s[40]; // [sp+80h] [bp-48h] BYREF
if ( !a4 )
return 0;
if ( !dword_707C )
{
v7 = (void *)sub_1390(&unk_5388, 32);
dword_7078 = sub_1630(a1, a3, v7);
free(v7);
dword_707C = 1;
}
if ( dword_7078 )
return 0;
v9 = *a1;
v10 = (*a1)->GetByteArrayElements(a1, a4, 0);
v16 = a4;
v11 = v9->GetArrayLength(a1, (jarray)a4);
v12 = (const char *)dword_7074;
if ( !dword_7074 ) // SALT位置, 是个char*指针
{
v12 = (const char *)sub_1390(&unk_5378, 16);
dword_7074 = (int)v12;
}
memset(s, 0, 0x21u);
v13 = strlen(v12);
sub_1EC0(v17); // 初始化MD5数组, 进入此函数有MD5常数
v15 = v10;
sub_1EF0(v17, v10, v11); // updateDigest
if ( v13 >= 1 )
{
for ( i = 0; i < v13; i += 2 )
{
sprintf(s, "%c%c", *(unsigned __int8 *)(dword_7074 + i), *(unsigned __int8 *)(dword_7074 + i + 1)); // 加SALT, SALT在dword_7074
sub_1EF0(v17, s, 2); // updateDigest
}
}
sub_1F80(v17); // MD5结束
// 将结果转为HEX
sprintf(s, "%02x", (unsigned __int8)v17[88]);
sprintf(&s[2], "%02x", (unsigned __int8)v17[89]);
sprintf(&s[4], "%02x", (unsigned __int8)v17[90]);
sprintf(&s[6], "%02x", (unsigned __int8)v17[91]);
sprintf(&s[8], "%02x", (unsigned __int8)v17[92]);
sprintf(&s[10], "%02x", (unsigned __int8)v17[93]);
sprintf(&s[12], "%02x", (unsigned __int8)v17[94]);
sprintf(&s[14], "%02x", (unsigned __int8)v17[95]);
sprintf(&s[16], "%02x", (unsigned __int8)v17[96]);
sprintf(&s[18], "%02x", (unsigned __int8)v17[97]);
sprintf(&s[20], "%02x", (unsigned __int8)v17[98]);
sprintf(&s[22], "%02x", (unsigned __int8)v17[99]);
sprintf(&s[24], "%02x", (unsigned __int8)v17[100]);
sprintf(&s[26], "%02x", (unsigned __int8)v17[101]);
sprintf(&s[28], "%02x", (unsigned __int8)v17[102]);
sprintf(&s[30], "%02x", (unsigned __int8)v17[103]);
v9->ReleaseByteArrayElements(a1, (jbyteArray)v16, v15, 2);
return v9->NewStringUTF(a1, s);
}Frida读SALT
请出我们万能的Frida!
let Core = Module.findBaseAddress("libcore.so")
let Ptr = Core.add(0x7074).readPointer()
console.log(hexdump(Ptr)) 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
ea102d40 37 37 32 38 36 37 63 31 39 39 32 35 00 00 00 00 772867c19925....
ea102d50 30 2e 10 ea f0 2d 10 ea 60 fc 29 e9 1c aa b0 b3 0....-..`.).....
ea102d60 f0 2d 10 ea 60 0c 23 e8 a0 fb 29 e9 00 00 00 00 .-..`.#...).....
ea102d70 d0 0b 23 e8 b0 2d 10 ea 00 18 0e d9 00 00 00 00 ..#..-..........注意到SALT为772867c19925
Python
Python代码如下:
import hashlib
SIG_SALT = b'772867c19925'
# QParams: GET参数, PParams (POST用Form形式传的参)
def Sig(QParams: dict, PParams: dict) -> str:
return hashlib.md5(''.join(sorted(f'{i[0]}={i[1]}' for i in sorted(QParams.items()) + sorted(PParams.items()))).encode() + SIG_SALT).hexdigest()
__NSTokensig参数
逆向
算法
Jadx搜索__NSTokensig, 易得
(此处是算法部分, 若要了解参数来源请往下看
public interface b {
/* renamed from: a */
Pair<String, String> mo74281a(String str, String str2);
Pair<String, String> computeSignature(Request request, Map<String, String> map, Map<String, String> map2);
/* compiled from: kSourceFile */
/* renamed from: com.yxcorp.retrofit.c$b$-CC, reason: invalid class name */
public final /* synthetic */ class CC {
public static Pair $default$a(b bVar, String str, String str2) {
return new Pair("__NStokensig", C35145d.m127705a(C35147a.m127718c(C35146e.m127709a(str + str2))));
}
}
}
跟进C35146e.m127709a中可发现, 此函数获取了str + str2的值
跟进C35147a.m127718c并继续跟进m127716b可得使用了SHA256
/* renamed from: c */
public static byte[] m127718c(byte[] bArr) {
return m127716b().digest(bArr);
}
private static MessageDigest m127716b() {
return m127717c("SHA-256");
}而C35145d.m127705a则将最后的结果转回了字符串
参数来源
参数: str, str2
XREFS寻找引用, 发现: $default$a -> mo74281a -> 3 more xrefs
如果你看得懂Java的话, 能够发现那三个用到的地方传参格式都是一致的
即: sig字符串 + CLIENT_SALT
// 部分代码节选
String mo104279v = m121891c.mo104279v();
boolean mo104282y = m121891c.mo104282y();
mo91180c(hashMap);
for (Map.Entry<String, String> entry : map.entrySet()) {
hashMap.put(entry.getKey(), entry.getValue());
}
String str2 = (String) mo104260c.computeSignature(request, hashMap, new HashMap()).second;
map.put("sig2", str2);
if (mo104282y && !TextUtils.isEmpty(mo104279v)) {
map.put("__NStokensig", (String) mo104260c.mo74281a(str2, mo104279v).second); // 第一个参数为sig, 第二个参数一路找过去你会发现就是如下代码
return;
}
// ----------我是"如下代码"----------
public final String mo104279v() {
return KwaiApp.f95073ME.getTokenClientSalt();
}Python
import hashlib
# 此函数依赖上一部分写的sig函数
def __NSTokensig(sig: str, ClientSalt: str) -> str:
return hashlib.sha256((sig + ClientSalt).encode()).hexdigest()
关于__NS_sig3
尝试
随便说几句(发癫):
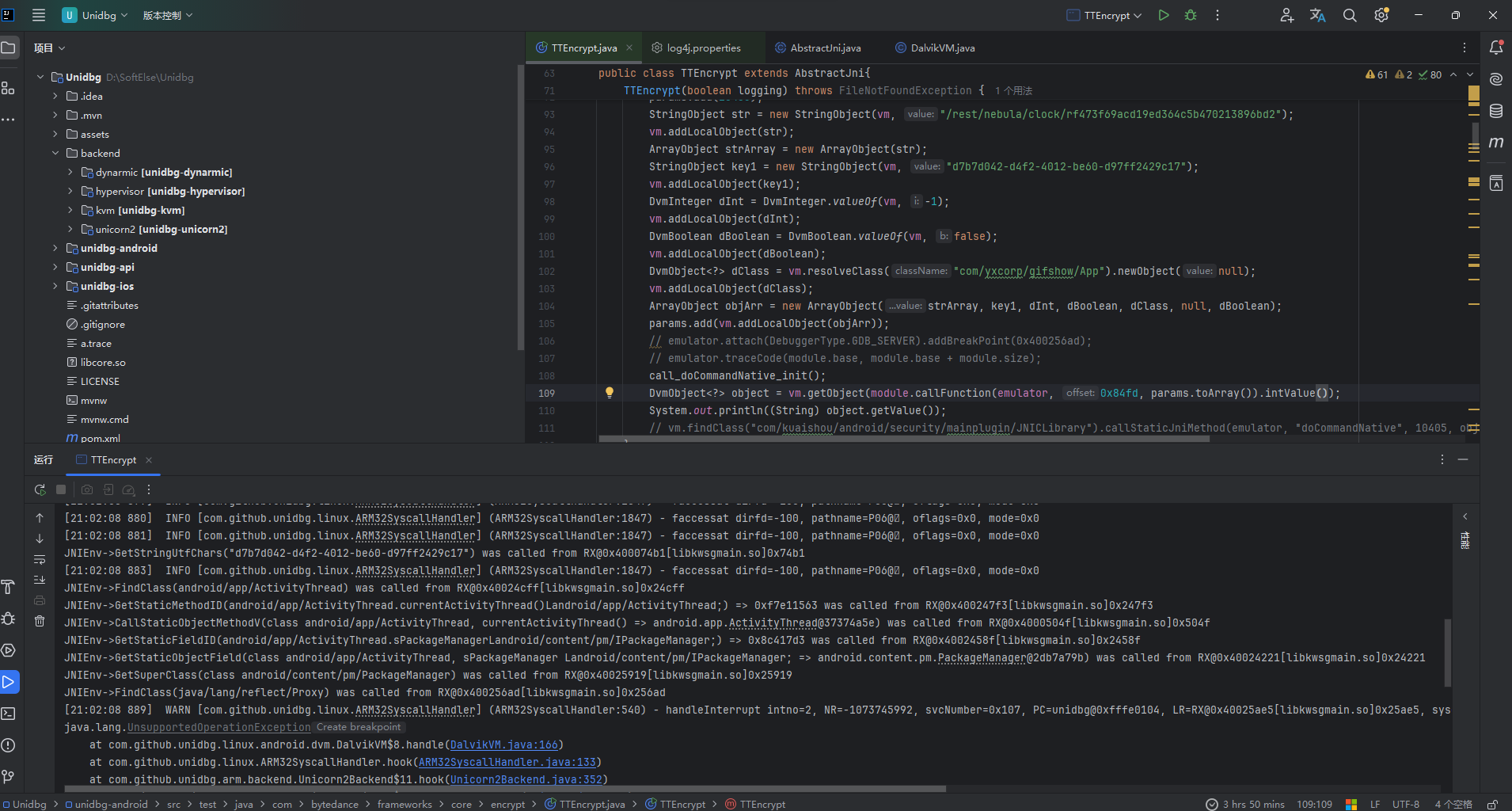
IDA打开一看, OLLVM混淆的稀碎, 控制流混淆太狠了吧....... JNI_OnLoad动态注册, 嗯, 合情合理......当时我还寻思, 要不, Unidbg试一下?
然后TM补环境补到炸啊!!!!!!!!! libkwsgmain.so你闲的没事FindClass(java/lang/reflect/Proxy)干啥啊!!!! 我这怎么补啊, 怎么寄的都不知道
你猜猜我当时骂那玩意骂了多久 :D
附笔者当时补环境的场景
可行方案
目前感觉可行一些的方案就是用Frida调用Java里的Native了, 补环境太费劲了
剩下部分自己去搜吧, 网上一大把